Popeax is a member of the Synack Red Team.
Often people think security research requires deep knowledge of systems and exploits, and sometimes it does, but in this specimen all it took was some marvel and a Google search to find an unsafely simple exploit using default credentials.
On a recent host engagement, I discovered an unusual login page running on port 8080, a standard but less often used HTTP port. The login page did not resemble anything I had encountered in the thousands of login pages wideness hundreds of vendee engagements.
Nothing new. Plane for a seasoned member of the Synack Red Team (SRT), it isn’t unusual to discover commercial products that one hasn’t seen before.
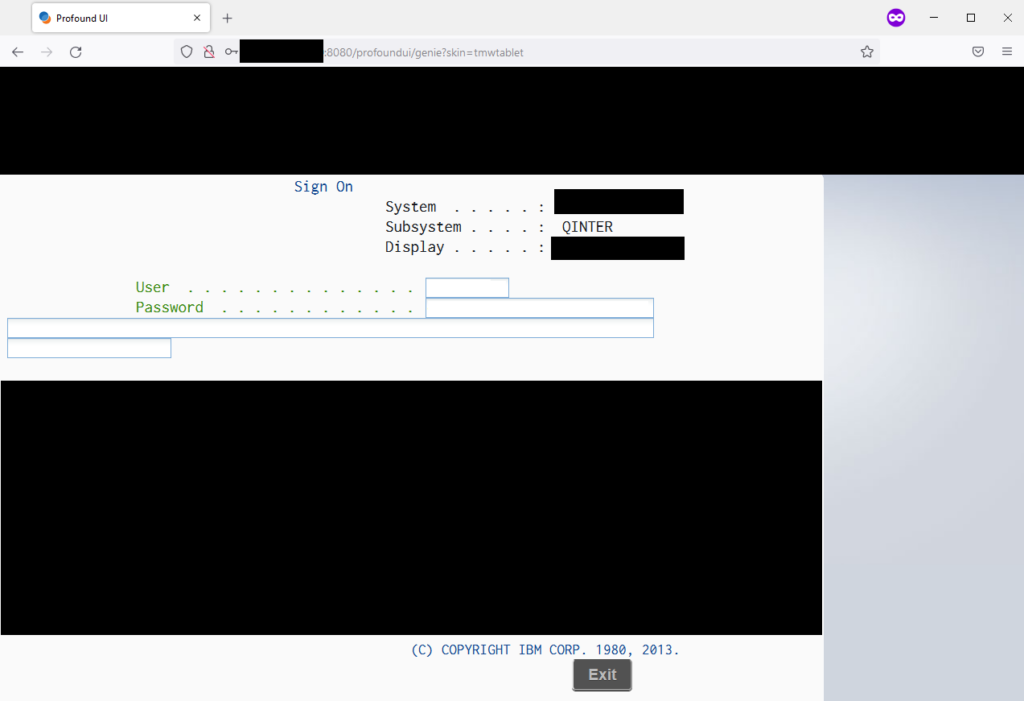
The login page unmistakably showed the product as some type of IBM server. In the URL, I noticed the string “profoundui.” A quick Internet search identified an IBM resource that stated:
“Profound UI is a graphical, browser-based framework that makes it easy to transform existing RPG applications into Web applications, or develop new rich Web and mobile applications that run on the IBM i (previously known as the AS/400, iSeries, System i) platform using RPG, PHP, or Node.js.”
Given these facts, I Googled for “IBM AS/400 default password” and found IBM documentation that listed default AS/400 credentials.
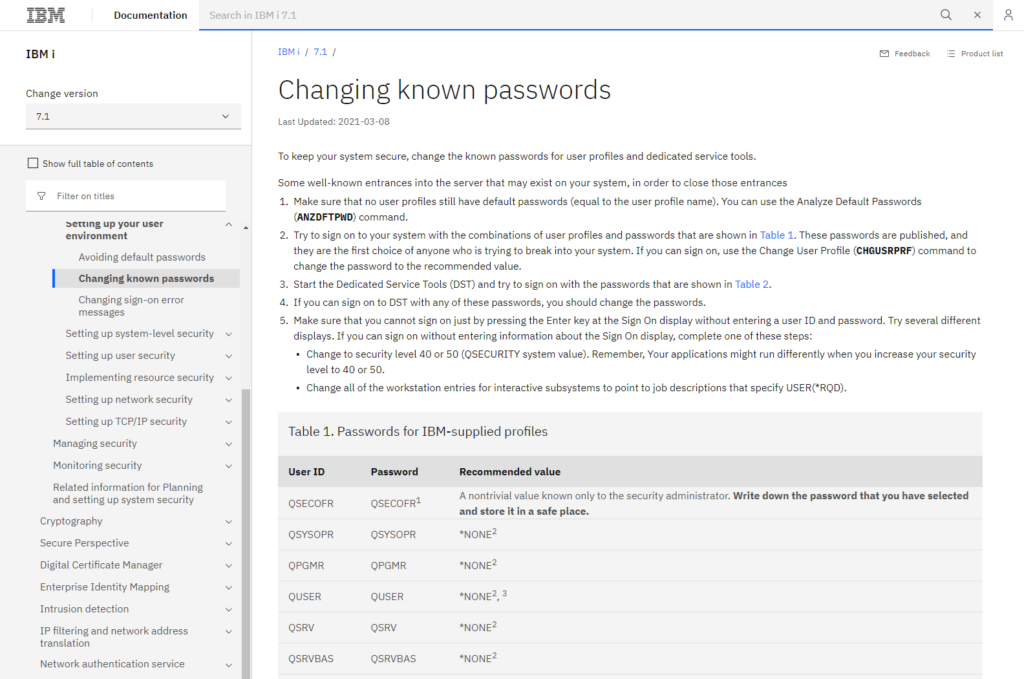
As any peerage hacker would do, I copied and pasted all six default usernames and passwords into the login form.
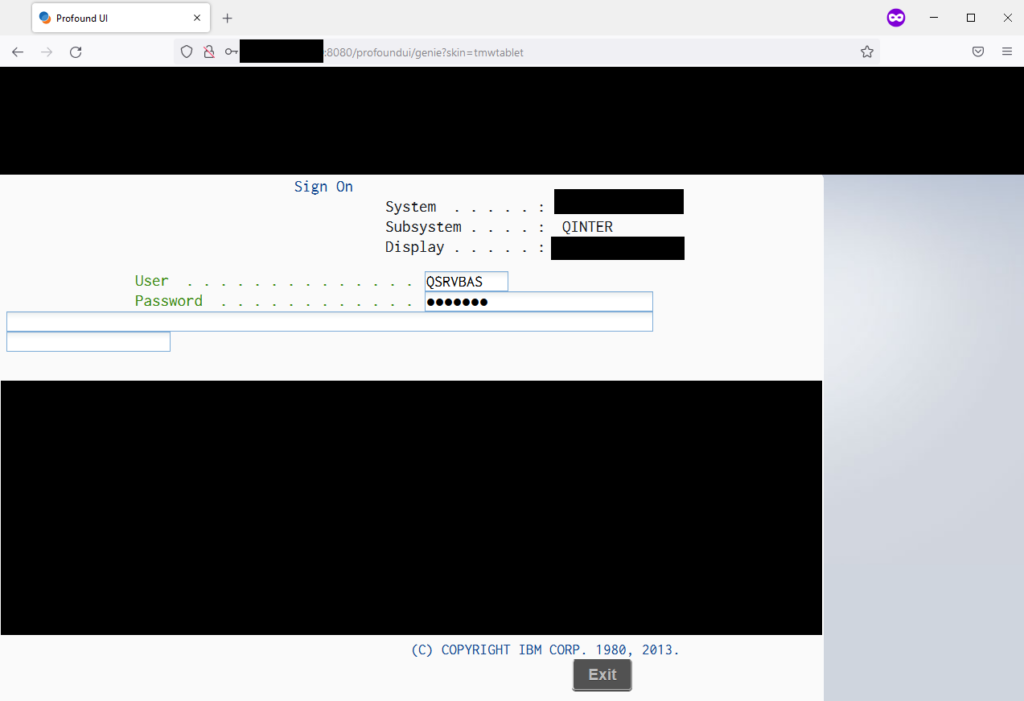
Sure unbearable the last set of credentials worked with user QSRVBAS and password QSRVBAS.
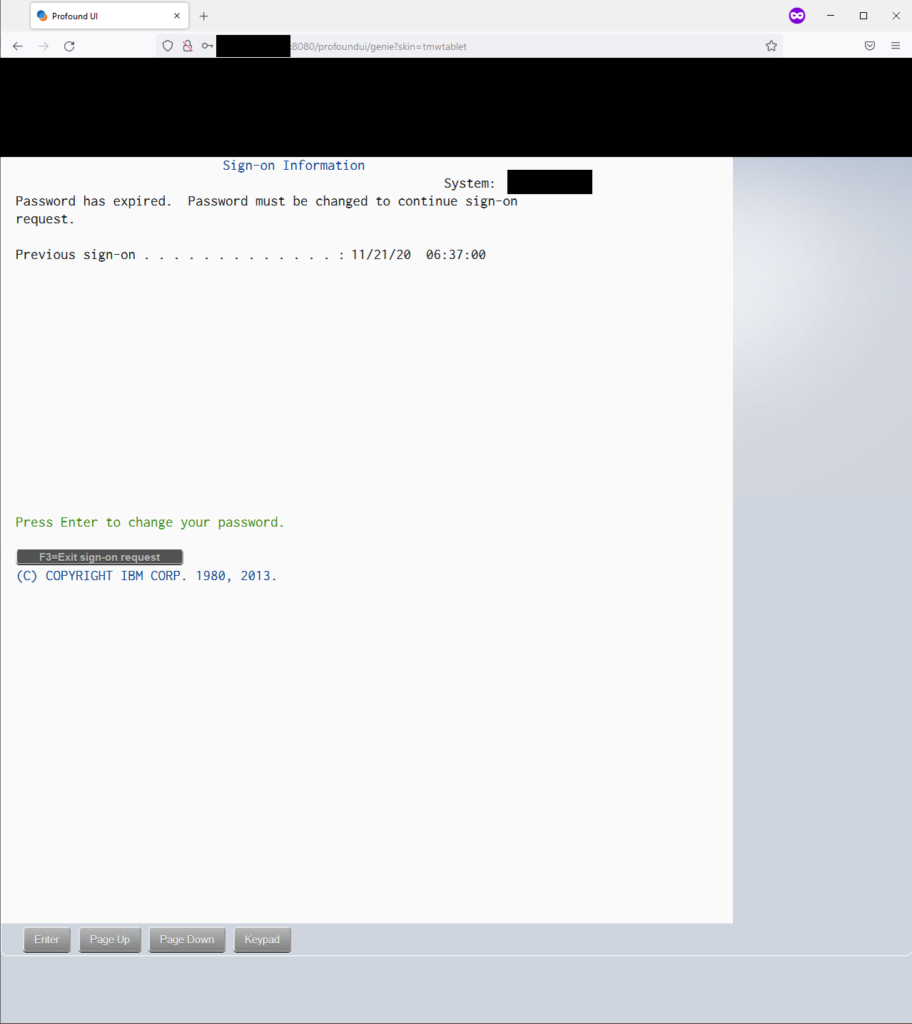
It was vastitude the telescopic of the engagement to proceed any remoter to see how much wangle was possible. The vulnerability was documented in the report that was given to the vendee to be remediated.
After a few days, the vendee requested a patch verification of the vulnerability using Synack’s patch verification workflow. This workflow allows a vendee to request the SRT to verify an implemented patch within the Synack Platform. After receiving the patch verification request, I quickly verified the vulnerability was no longer exploitable.
It is nonflexible to believe, but plane today commercial products still ship and are installed with default credentials. Often the onus is on the end user to be enlightened they must transpiration the credentials and lock the default accounts.
The ingenuity and marvel of the SRT cannot be replicated by scanners or streamlined technology. The SRT members are whiz at finding this type of vulnerability in custom and commercial applications, plane while running in obscure locations, which leads to exploitable vulnerabilities stuff surfaced to the customer.
The post Exploits Explained: Default Credentials Still a Problem Today appeared first on Synack.