The idea of creating Web 3.0 has been virtually since the end of 2000s. The new version of the world wide web should repair the weak points of Web 2.0., some of which are: featureless content, prevalence of proprietary solutions, and lack of safety in a internal user data storage environment, where a massive leak is likely should just one server be compromised. Web 3.0 is described as a decentralized and unshut internet — some of its features once implemented in today’s digital world.
Unfortunately, the “new internet” will still remain a playground for criminals who will employ cutting-edge technologies for their old sport of data theft, financial machinations and the like. In this article, I will dwell on how they use one of the WEB 3.0 technologies — the distributed file system IPFS — for email phishing attacks.
What is IPFS?
IPFS (InterPlanetary File System) is a peer-to-peer distributed file system enabling users virtually the world to mart files. Unlike internal systems, IPFS uses addressing performed equal to unique content identifiers (CID), and not file paths. CID is generated based on the file’s hash value and then recorded to a distributed hash table, which moreover contains information on the file owner. The file itself resides on the computer of the user who had “uploaded” it to IPFS, and is downloaded directly from that computer. The structure of IPFS is somewhat similar to the BitTorrent protocol which, too, is a distributed network where file mart takes place directly between the users’ devices.
By default, uploading a file to IPFS or downloading it requires special software (IPFS client). For users to view the files residing in IPFS freely without installing any software, the so-called gateways are provided. A gateway is in fact a server with wangle to IPFS. To unshut a file via a gateway, a URL is required normally containing a gateway address, reference to IPFS, and the file’s CID. URL formats can be quite different, for example:
- https://gateway_address/ipfs/CID
- https://CID.ipfs.gateway_address
Phishing and IPFS
In 2022, scammers began urgently using IPFS for email phishing attacks. They would place HTML files containing a phishing form in IPFS and use gateways as proxies, so that victims could unshut the file, whether or not running an IPFS vendee on their devices. The scammers would include file wangle links via a gateway into phishing reports dispatched to would-be victims.
The use of a distributed file system allows attackers to cut when on phishing page hosting costs. Besides, you cannot delete files uploaded by third parties from IPFS. If somebody wants a file to disappear from the system completely, they can urge its owners to delete it, but the method will probably never work with cybercriminals anyway.
IPFS gateway providers struggle to gainsay IPFS phishing by regularly deleting links to fraudulent files.
Phishing page deletion notification
Yet detection and deletion of links at gateway level does not unchangingly happen as quickly as the blocking of a phishing website, deject form, or document. We have observed URL addresses of IPFS files that first appeared in October 2022 and remain operational at the time of this writing.
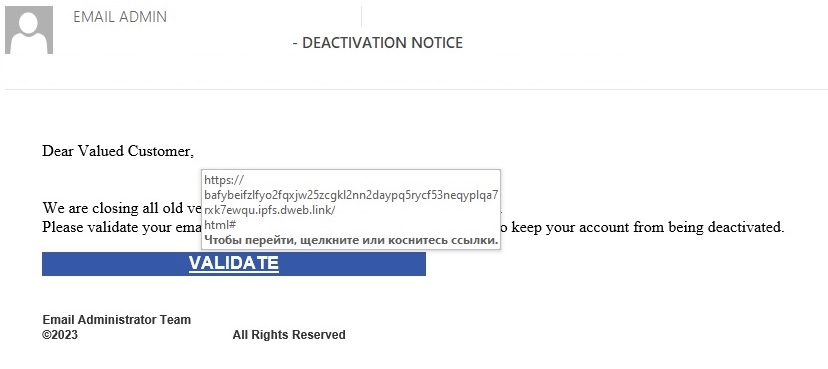
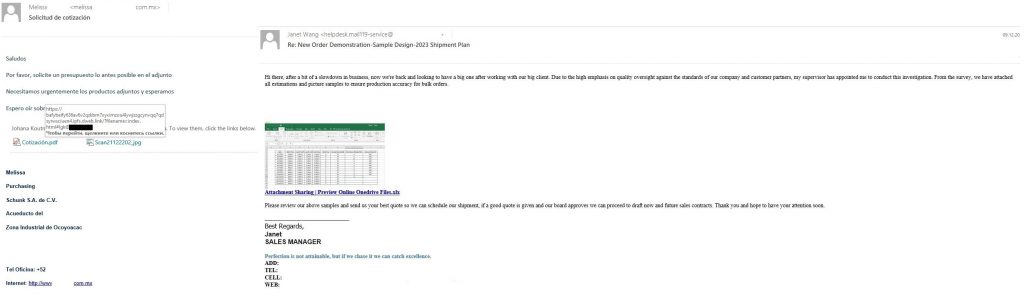
Phishing reports containing IPFS links are whimsically overly too original — they contain the typical phishing content the purpose of which is to obtain the victim’s worth login and password.
Phishing letter with an IPFS link
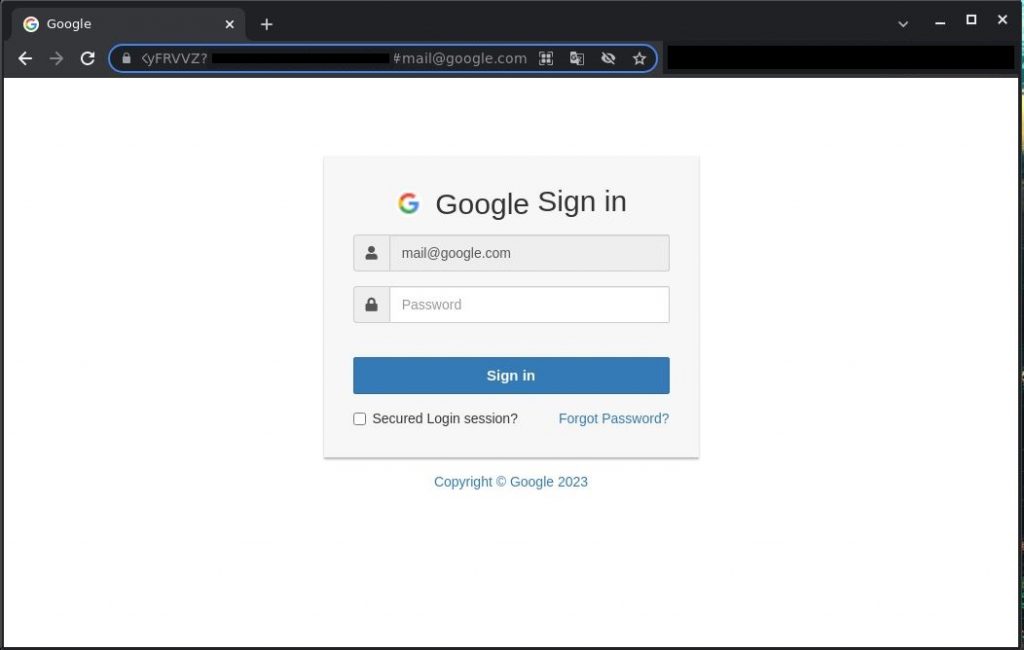
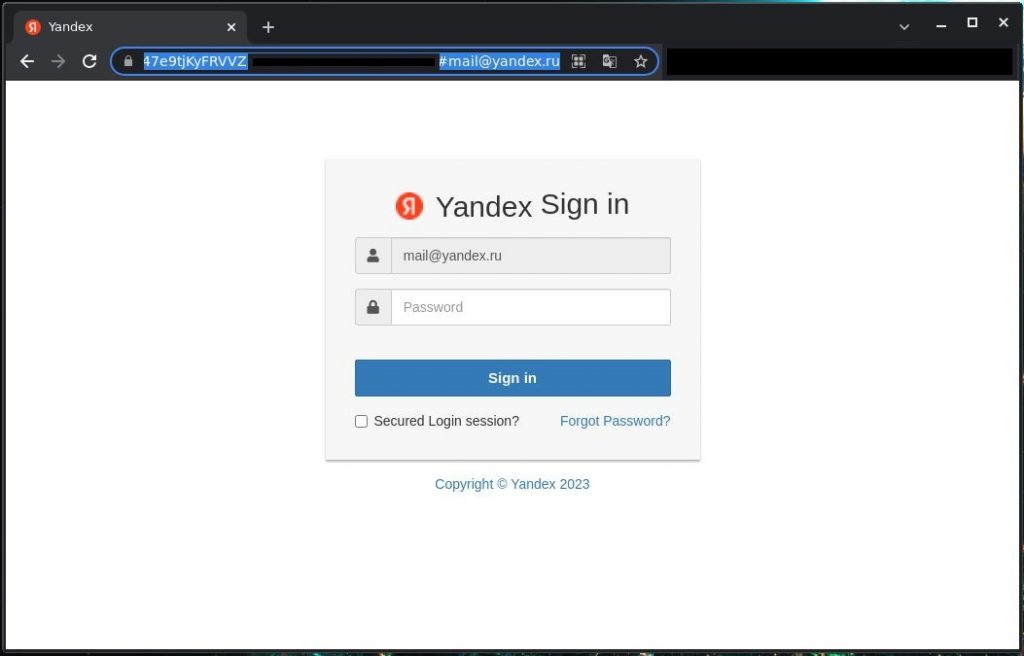
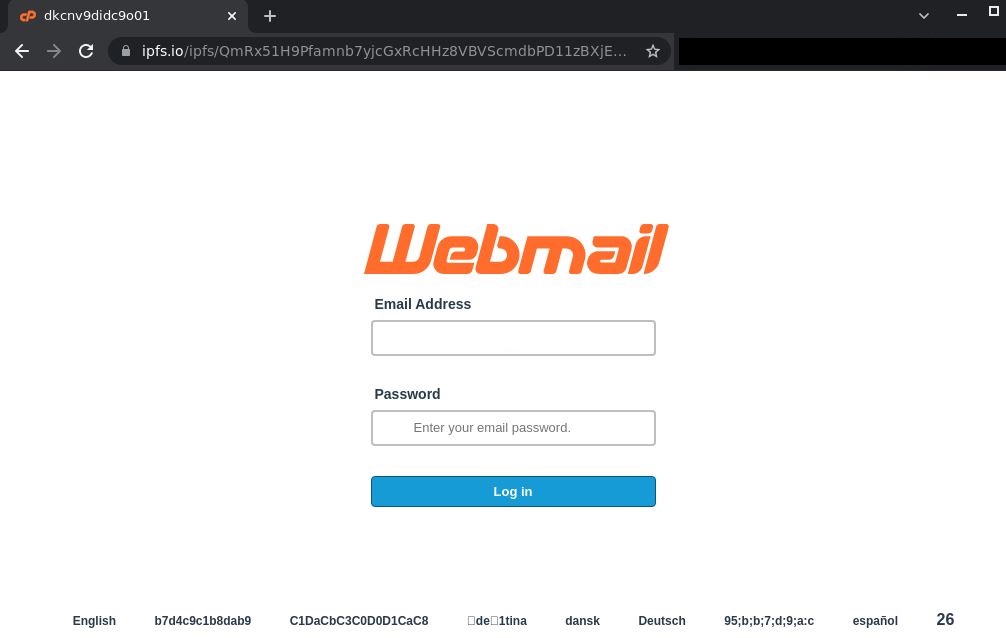
It is a bit increasingly interesting to examine the HTML pages the links lead to.
HTML page used for phishing
As can be seen on the screenshot above, the URL parameter contains the recipient’s e-mail address. Once it is modified, the page content will transpiration too: the corporate logo on top of the phishing form and the email write entered into the login field. In this way, one link can be used in several phishing campaigns targeting variegated users — sometimes plane in dozens of campaigns.
Phishing page modification
The logo replacement effect is achieved using a simple JavaScript code. The script obtains domain info from the page URL parameter and substitutes it into the URL of the Google resource, from which a logo icon is then sourced.
Company logo substitution
Use of IPFS in targeted phishing attacks
The use of IPFS is not limited to mass mailing campaigns: it is used for ramified targeted attacks too. Unlike the ordinary ones, targeted phishing campaigns are much largest prepared, normally focusing on specific persons within the company, not just random users.
Targeted phishing with an IPFS link
In the two examples above, the attacks were leveled at corporate procurement departments, the reports coming from sales managers of existing organizations. The phishing page itself lacks in originality.
Phishing page used in a targeted attack
Statistics
In late 2022, we were observing 2–15 thousand IPFS phishing reports a day for most of the time. But there were quieter days too. Thus, our systems registered only 637 such reports on December 1, and 937 on December 23. Starting this year, IPFS phishing began to grow in scale. We observed a few upsurges in January and February with over 24,000 reports a day — with peaks reaching 34–37 thousand/day. However, the flurry has died lanugo little by little by mid-February, the number of attacks mostly returning to November and December levels.
Dynamics of the number of IPFS phishing attacks, November 2022 — February 2023 (download)
Yet it is worth noting that February turned out the busiest month in terms of IPFS phishing activity. In that month alone, we observed scrutinizingly 400,000 letters — increasingly than 20,000 whilom the January figure, and over 100,000 increasingly than in November and December 2022.
IPFS phishing reports distribution by month, November 2022 — February 2023 (download)
Conclusion
Attackers have used and will protract to use cutting-edge technologies to reap profits. Of late, we observe an increase in the number of IPFS phishing attacks — both mass and targeted. The distributed file system allows scammers to save money on domain purchase. Plus, it is not easy to completely delete a file, although, there are attempts to gainsay fraud at IPFS gateway level. The good news is that anti-spam solutions snift and woodcut links to phishing files in IPFS, just like any other phishing links. In particular, Kaspersky products employ a number of heuristics to snift IPFS phishing.